Using RAW Komunikator, you benefit from:

Intrusion detection. Automated locking feature
Data confidentiality under control. Communication via your secure on-premises server
Encrypted voice calls, text messages, chats, document transmission
Private internal phone book accessible to RAW Komunikator user only

Download RAW Komunikator
RAW Komunikator available on platforms
Encryption technology
All communication between two internal applications is encrypted end-to-end. Messages sent through the secure communication channel go through the server, which works as a00A0proxy. "End-to-end encryption" means that no transmitted message can be decrypted by anyone else than its intended recipient – neither the server nor any third party who manages to intercept it.
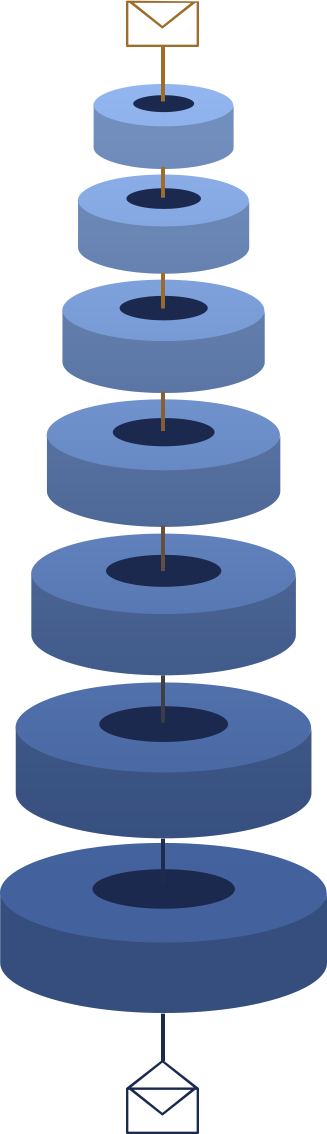
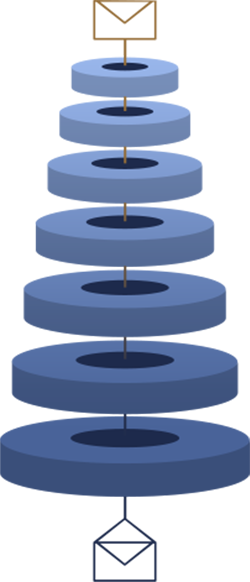

Distributed encryption key
Local data is protected and encrypted with a00A0distributed encryption key.
Secure channel
Two devices build a single secure channel with different keys for each communication session.
Trusted encryption components
Cryptographic core and encryption protocols are based on X25519, XSalsa20, ChaCha20 and Ed25519.
Double ratchet
Part of the cryptographic core that ensures end-to-end encryption.
Secure transport layer
The entire traffic between the server and the client is secured by TLS. The process ensures server authentication.
Authenticated communication
The entire communication relies on a mutual authentication mechanism that involves both the server and the client.
Secure message dispatcher
The server can only send messages and set up the channel between authenticated devices (contacts).
- Full control over the entire on-premises infrastructure
- Full end-to-end encryption
- No content stored on the server
- RASP (Runtime Application Self–Protection)
- Obfuscation of the application code
- Attestation
- Distributed management of the private session key
- The key is never stored in non-volatile memory
- The key is only present in RAM for the short moment while the cryptogram is being built